Get the last ‘lulz’: Verify Lotus Domino security with your Ytria toolkity
A spate of major digital security breaches have made worldwide headlines in the past year. In some cases, the cyber attacks were undertaken by politically motivated ‘hacktivists’; others attacks were criminal in nature; in other cases, the perps were arguably mischief-makers above all else.
These events must have been miserable for the IT staffers at the affected organizations. Certainly a lot of admins were left with red faces in the wake of these incidents but you’ve got to wonder how many had their professional reputations ruined or even lost their jobs in the aftermath.
The Yellow Brick Wall?
But we’re in the Lotus Notes world and Notes is synonymous with security, right? How does this affect us?
Well, nobody’s perfect and the very human aspects of administering Notes/Domino leave us with a number of areas where oversight or human error can potentially compromise Domino security.
Another Notes blog recently posed the question “Has Lotus Notes ever been hacked on a large scale?”; though none of the commenters named a successful major attack from the outside on a Lotus Notes network, it was acknowledged that administration mishaps can leave your organization vulnerable to hackers from the outside and particularly on the inside (comment #5 is a particularly interesting and funny example that illustrates what can go wrong when the ‘Allow use of stored forms…’ property–more on this later–is enabled on a database that has an overly loose Execution Control List).
Words from the Wise
What really got us thinking about all this was that some of our own customers recently shared interesting security-related anecdotes with us; like the following:
- One admin told of how the first time he used agentEZ, its grid interface (which can show all the agents on all the databases on a Domino server) allowed him to spot a suspicious agent. Further investigation revealed that an employee had created this rogue agent for the sole purpose of stealing sensitive company data!
- Another decided to do a little test to see how far he get into his own company’s network through anonymous Web access–he was startled to find out that anonymous users could potentially access vast portions of their system from the outside. He used aclEZ to quickly locate and fix the security holes; he used databaseEZ to get an overall view of all the databases that were accessible from the Web (i.e. the ‘Don’t Allow URL Open’ NSF property was unchecked–more on this later)
- Another customer told us how he gasped when he first used scanEZ and saw how lax the security was on some of his company’s extremely sensitive databases. Mere obfuscation measures like using ‘hide-when’ attributes on form fields and views were being used to sweep sensitive data ‘under the rug’ instead of making use of true Lotus Notes security.
With all this in mind, we decided to share some quick tips on how you can use Ytria tools to help ensure your Domino environment is more secure:
Managing global NSF properties with security implications
databaseEZ‘s grid interface lets you keep tabs on nearly 100 Lotus Notes database properties for all your databases across an entire Domino server. It so happens that a number of of these global NSF properties can have a bearing on security, like the following:
- Don’t Allow URL Open*:
-
- One of the most basic security considerations is ensuring that your applications are only accessible from the Web where it is appropriate. Read more on this
-
- User Activity – Is Recorded/User Activity – Is Confidential*: The former lets you know if user activity is set to be recorded for a given database; the latter limits access to this (possibly sensitive) data. To read more about this property and the potential disk space/security tradeoffs that are necessary to consider, click here.
- Maintain LastAccessed Property*: When this property is enabled, the “Accessed (in this file)” stamp will be updated each time a document is read OR modified thereby giving you a way to track activities in your environment at a certain level. If it’s not enabled the stamp will only be updated when modifications occur. (Warning: Enabling this property can also lead to a significant performance hit in some instances– read more here).
- Require SSL Connections*: Forces encrypted communication between Web browsers and the server. In other words, the property helps ensure that databases used on the Web are used in a secure manner. Read more here.
- Allow Domino REST API Operations: When enabled, remote for API calls could potentially be executed in some instances. Here’s a good overview to get started on this topic.
- Allow Use of Stored Form in this Database: When this property is disabled, code contained in a document’s stored form won’t be able to run. If enabled, any stored form code may or may not be able to run depending on the ECL settings.
- Disable background agents for this database*: This is one of your most basic security options; with this checked, there’s no chance of rogue background agents running.
- Disable export of view data: For databases with sensitive information, it can be a good idea to set this property in order to make it more difficult for someone to hastily steal large amounts of data.
Note: Properties marked with an asterisk (*) are retrieved using summarized data so they appear instantly. To see the remaining properties you must click Ctrl+L to load detailed information.
Not all of these properties are shown in the grid by default so you must use the Grid Data Composition panel to customize databaseEZ’s interface. Once they’re shown in the grid, just drag any given property’s column header to the ‘grouping area’ to sort the databases by said property.
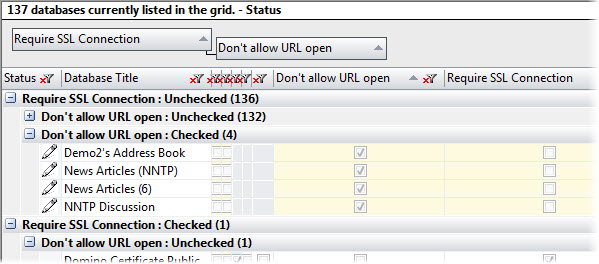
An example of multiple-level grouping in databaseEZ
You may find it helpful to use the Grid Data Composition panel’s Save feature to keep these properties as a sort of ‘security audit’ set in databaseEZ (Note: similar feature is available in agentEZ).
If you’ve never tried this feature, it’s very straightforward:
1) Go to the Grid Data Composition panel and select the security-related database properties you’d like to use along with any informational properties you’ll need (e.g. Database Title) and then click Apply.
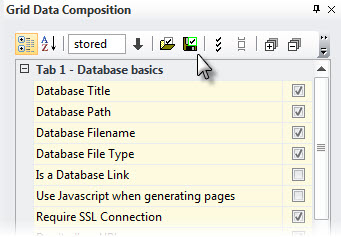
2) Next click the Save button to save your preference file to disk (Tip: since databaseEZ’s grid supports about 100 database properties, you may want to save several sets for different administration tasks). Just click the Load Preference button to retrieve saved property sets.
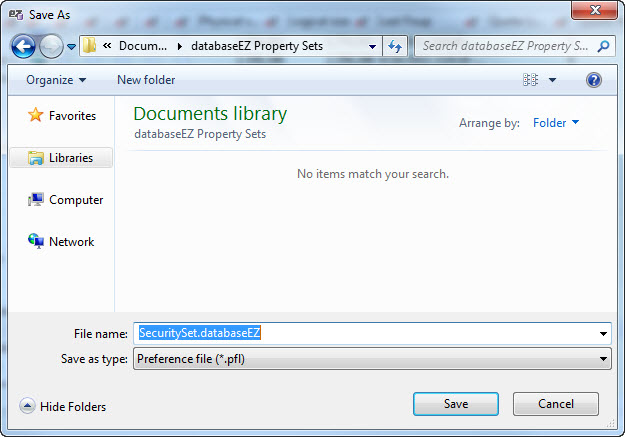
Saving sets of columns to use in databaseEZ’s grid; agentEZ offers a similar option for saving set of agent property columns
Instant reports: Export your findings to a spreadsheet
One very handy feature that’s available in databaseEZ and most other Ytria tools is the ability to export (or copy and paste) any data that’s displayed in our grid-type windows or panels. You’ll find this helpful when creating reports based on information shown in the tools.
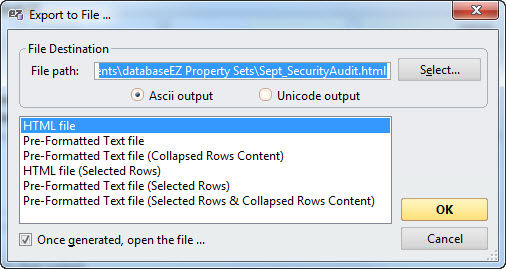
To export your data, you can simply click Ctrl+C to copy any selected rows to the clipboard (the column headers will also be copied) and paste to Excel or any other spreadsheet or text editor. For more advanced exportation options, just right-click in the grid and choose Grid Actions>Export.
Getting a bird’s-eye-view of the ACLs on your servers
Making use of grouping by column headers in aclEZ’s grid interface can come in very handy when trying to get an overall view of a Domino server’s security.
For instance, grouping by ‘Name‘ lets you see a given ACL entry’s complete access across the server. This can be handy for spotting inappropriate access (e.g. an employee who’s switched departments a few times may find themselves with extraordinary access).
To look at things from an ‘access’ perspective, you can sort by Name>Access columns. This lets you quickly spot oversights like giving Default Manager access. There was an earlier Ytria Tech Lab post that goes through this is more detail, read it here.
The grid in aclEZ also provides a convenient way to manage the various ACL attribute checkboxes across a server, as shown below:
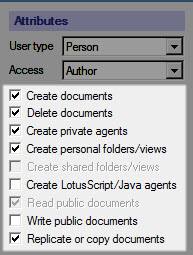
The checkboxes under ACL Attributes in Notes form an integral part of your Domino environment’s security
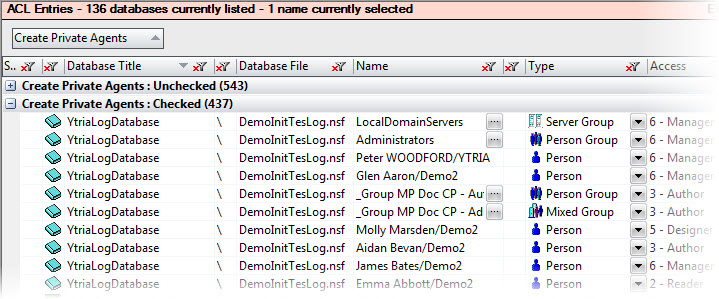
aclEZ lets you look at your entire server from an access perspective
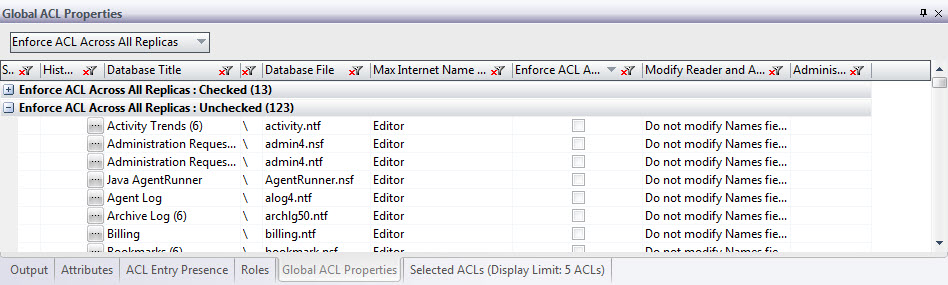
Another handy security feature in aclEZ is the Global ACL Properties tab. The information shown here can be helpful for spotting security vulnerabilities. The ‘Enforce a consistent Access Control List across all replicas’ (which can help ensure that databases that have been tampered with locally are not replicated) and ‘Maximum Internet name and password’ properties are particularly deserved of an admin’s attention.
Manage all the agents running on a server
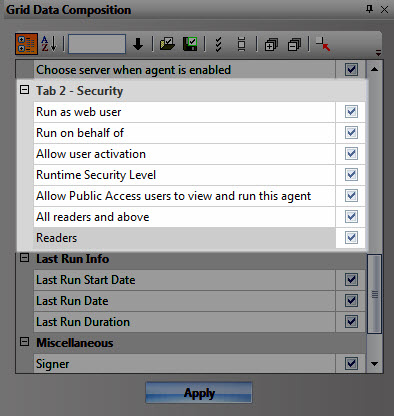
The serverwide vision provided in agentEZ’s grid is also be very useful in the realm of Domino security. On its most basic level, just seeing all the agents (along with their properties and runtime information) in a single screen can help you spot suspicious agents (including private agents).
It’s particularly handy to look at the agent ‘Security’ properties (i.e. the same properties shown in the ‘Security’ tab on the Agent Properties dialog in Notes). To focus on these agents’ properties, you can create a ‘security set’ in the same manner as we described for databaseEZ earlier in this post.
How are you using the tools in connection with security?
This post was just intended to show a few of the very simple ways you could use Ytria tools in relation to Domino security. We’d love to hear more on how you’re using your Ytria tools for security-related jobs.
Please contact us or comment below to share your tips or stories.


Submit a comment